There's normally some added action or two needed to adopt a more secure way of Doing the job. And most people don't like it. They actually want lower security and the lack of friction. That is human character.
We make this happen using the ssh-copy-id command. This command will make a connection into the remote Pc similar to the normal ssh command, but in lieu of enabling you to log in, it transfers the general public SSH vital.
If your message is successfully decrypted, the server grants the consumer accessibility without the have to have of a password. The moment authenticated, end users can launch a distant shell session in their local terminal to provide textual content-based mostly instructions on the distant server.
Be aware that though OpenSSH need to function for A selection of Linux distributions, this tutorial continues to be analyzed utilizing Ubuntu.
Although passwords are sent to your server in a very safe method, They can be typically not intricate or very long plenty of to generally be proof against repeated, persistent attackers.
Our mission: to help you persons figure out how to code without spending a dime. We execute this by building Many movies, content articles, and interactive coding lessons - createssh all freely accessible to the general public.
The remote Pc now recognizes that you should be who you say you might be due to the fact only your personal crucial could extract the session Id in the information it sent to your Laptop or computer.
ssh-keygen is often a command-line Software accustomed to crank out, control, and transform SSH keys. It permits you to generate safe authentication qualifications for distant entry. You are able to find out more about ssh-keygen And exactly how it really works in How to develop SSH Keys with OpenSSH on macOS or Linux.
Help you save and close the file while you are finished. To truly carry out the adjustments we just created, it's essential to restart the service.
-t “Kind” This feature specifies the kind of crucial to get made. Usually made use of values are: - rsa for RSA keys - dsa for DSA keys - ecdsa for elliptic curve DSA keys
This is how to make every one of the SSH keys you'll ever need to have using three diverse approaches. We'll provide you with how you can make your Original list of keys, in addition to further types if you would like produce distinct keys for a number of web-sites.
In any larger sized Firm, usage of SSH crucial administration answers is sort of essential. SSH keys must also be moved to root-owned locations with right provisioning and termination processes.
The tool is additionally employed for generating host authentication keys. Host keys are saved from the /etcetera/ssh/ Listing.
After the above mentioned disorders are legitimate, log into your remote server with SSH keys, either as root or with the account with sudo privileges. Open the SSH daemon’s configuration file:
 Haley Joel Osment Then & Now!
Haley Joel Osment Then & Now!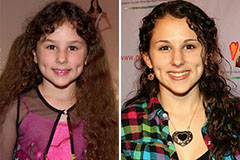 Hallie Eisenberg Then & Now!
Hallie Eisenberg Then & Now! Tahj Mowry Then & Now!
Tahj Mowry Then & Now! Danielle Fishel Then & Now!
Danielle Fishel Then & Now! Andrew McCarthy Then & Now!
Andrew McCarthy Then & Now!